The strategy for storing cryptocurrencies is critical for the secure management of your digital wealth. It demands as much attention and careful investigation as the decision-making process involved in purchasing crypto assets. The tales of staggering losses due to compromised exchange platforms often highlight the vulnerability of Hot Wallets. It’s time to delve into the world of Hot Wallets, recognize their utility, and importantly, discern when it’s wiser to transfer our holdings to more secure storage options.
What is a Hot Wallet?
A Hot Wallet is a type of cryptocurrency wallet that stays connected to the internet, enabling online accessibility for transactions and various activities. In contrast, cold wallets, or ‘cold storage,’ keep cryptocurrencies offline, offering enhanced security for storing digital assets.
Hot wallets find extensive use among individuals, businesses, and cryptocurrency exchanges, providing a convenient means for swift transactions. They are particularly suitable for holding smaller amounts of cryptocurrencies designated for everyday use, such as purchasing goods and services or engaging in trading activities on exchanges. The internet connection allows users to access their funds seamlessly across multiple devices, including computers, smartphones, and tablets.
Why Choose a Hot Wallet?
Hot wallets are preferred by individuals for various reasons, primarily due to their convenience and accessibility across different devices.
- Simplicity and Accessibility: Internet-connected hot wallets provide users with easy access to their funds on various devices, including computers, smartphones, and tablets. Their flexibility is particularly advantageous for regular transactions and daily operations;
- Rapid Transactions: A key advantage of hot wallets is their ability to support swift transactions. This speed is vital for online purchases, settling bills, and trading cryptocurrencies on exchanges, offering faster confirmation and processing times than other transaction methods;
- Intuitive Design: Hot wallets often come with interfaces that are straightforward, making them ideal for those new to cryptocurrencies. They usually include features that make sending and receiving digital currencies a breeze;
- Seamless Exchange Connectivity: Many cryptocurrency exchanges offer hot wallets to their customers. These wallets are built into the exchange platforms, allowing for effortless transfers between the exchange and the wallet, which facilitates trading and cashing out;
- Suitability for Regular Use: Hot wallets are well-suited for holding smaller cryptocurrency amounts intended for regular use. People who use Bitcoin or other digital currencies for everyday online shopping find hot wallets a handy and efficient option;
- Participation in Staking and DeFi: Some hot wallets are equipped to support staking and participation in decentralized finance (DeFi) initiatives, providing users with chances to earn rewards or interest on their digital currencies. Accessing these features is typically more straightforward with hot wallets.
While hot wallets offer numerous advantages for users seeking quick and easy access to their cryptocurrencies, it’s essential to recognize the vulnerabilities associated with these wallets. Understanding these vulnerabilities is crucial for both current crypto holders and prospective investors.

Risks in Cryptocurrency Hot Wallets: What You Need to Know
Cryptocurrency hot wallets, being online and connected to the internet, pose inherent risks primarily associated with vulnerability to hacking and unauthorized access. It’s essential to emphasize that hot wallets, by their nature, are susceptible to various cyberattacks, putting the stored funds at risk. Instances of significant cryptocurrency losses have occurred due to security breaches and hacking attacks on hot wallets, affecting both exchanges and individuals.
Furthermore, it’s crucial to note that leaving crypto assets on exchanges often means entrusting them to hot wallets, especially under the custody of the exchange. The unfortunate example of FTX and the substantial cryptocurrency losses suffered by its users serves as a stark reminder of the dangers associated with leaving assets on exchanges. If the exchange faces issues, there’s a likelihood that your assets might be compromised.
To mitigate these risks, users and exchanges must implement robust security measures. This includes incorporating multi-factor authentication, encryption, regular security audits, and restricting the amount of funds stored in hot wallets for day-to-day transactions. Larger cryptocurrency holdings should be secured in cold wallets, which are offline and less susceptible to online attacks. Additionally, users should exercise caution with the software they use, ensuring it comes from reputable sources and is regularly updated to protect against known vulnerabilities. Staying vigilant and proactive in implementing security measures is crucial in safeguarding cryptocurrency assets from potential risks associated with hot wallets.
Secure Alternatives to Cryptocurrency Hot Wallets
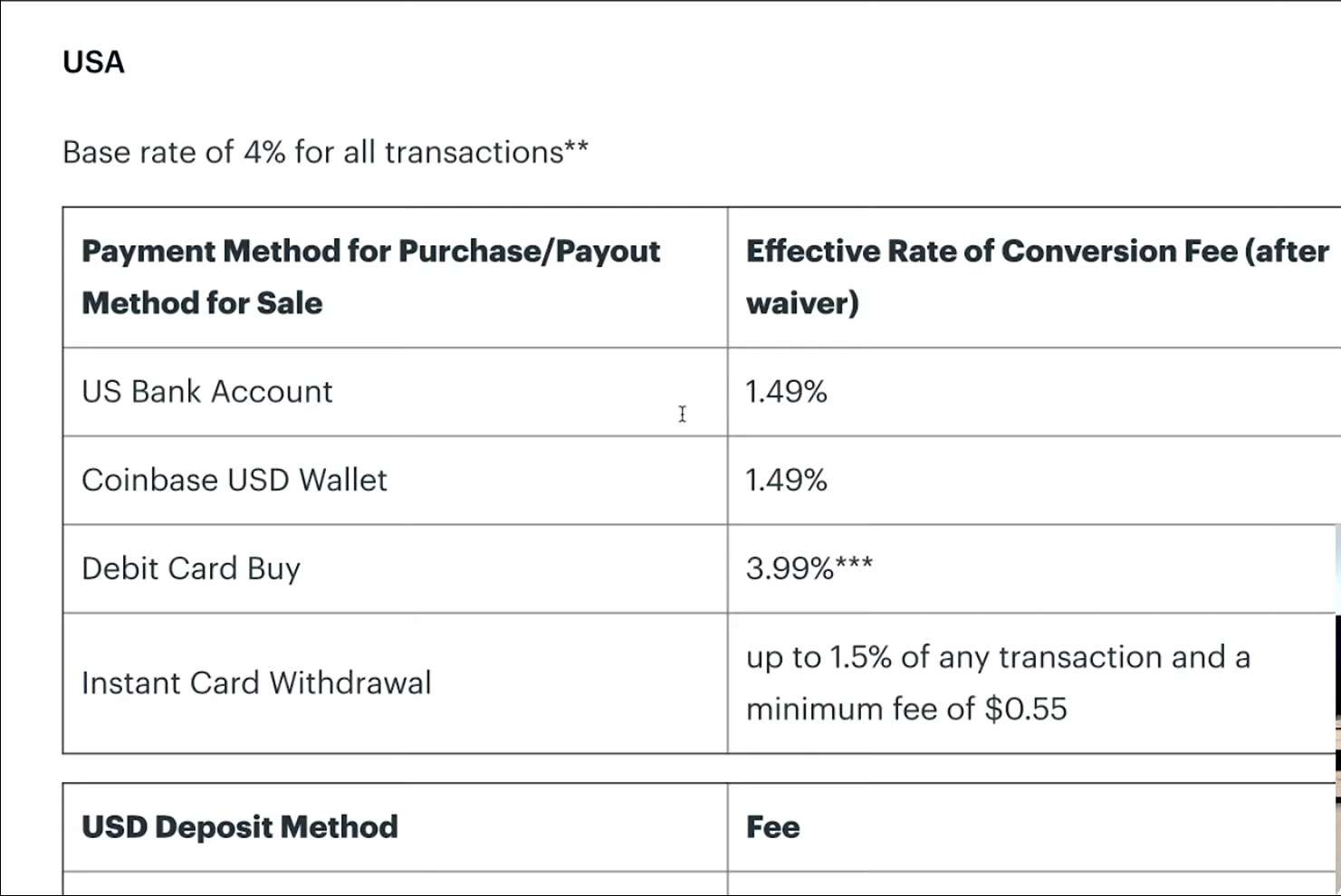
| Feature | Hot Wallet | Cold Wallet |
|---|---|---|
| Internet Connection | Connected to the internet | Not connected to the internet |
| Accessibility | Easy to access and use | Less accessible, requires additional steps to access |
| Security | More vulnerable to security breaches and hacking attempts | Provides the highest level of security |
| Offline Storage | Not applicable | Private keys are kept offline |
| Risk of Hacks and Theft | High | Low |
| Control | Relies on third-party providers for security measures | User has full control over private keys |
| Initial Investment | May require minimal investment or no investment | May require an initial investment to purchase hardware device or print out a paper wallet |
For individuals prioritizing enhanced security in the management of their cryptocurrencies, the most advantageous substitutes for a cryptocurrency hot wallet reside within the domain of cold wallets. Diverging from their online counterparts, cold wallets function offline, presenting a heightened level of security by disengaging from the internet. They stand out as an optimal selection for preserving substantial amounts of cryptocurrencies over an extended period.
A widely recognized form of cold wallet is the Hardware Wallet, a tangible device designed to securely store a user’s private keys offline. These hardware wallets, resembling USB drives and exemplified by Ledger Nano S, Ledger Nano X, and Trezor, are widely regarded as some of the most secure choices for extended cryptocurrency storage. The inherent offline status of hardware wallets acts as a safeguard against online hacking attempts, establishing a robust defense mechanism against potential security breaches.
Although cold wallets provide heightened security by being impervious to online attacks, it’s essential to acknowledge the responsibility tied to safeguarding the physical device. The loss of access to a cold wallet, lacking a backup, could result in the irreversible forfeiture of stored cryptocurrencies. As a precautionary measure, users should consider creating recovery phrases or maintaining multiple copies of paper wallets in secure locations to mitigate such risks. Opting for secure alternatives and implementing judicious measures ensures a resilient defense against potential vulnerabilities associated with the storage of cryptocurrencies.
Conclusion
Hot Wallets provide a highly convenient and user-friendly method for storing cryptocurrencies, particularly for day-to-day activities like transactions and trading. However, it is imperative for holders to remain cognizant of the inherent vulnerabilities associated with these wallets due to their online connectivity. When safeguarding a significant investment or a long-term crypto portfolio, crypto investors should explore the option of cold storage. This approach helps shield assets from vulnerabilities, allowing investors to take full self-custody of their investment and enhance overall security.